AWS GuardDuty Findings Ingestion in Splunk using S3 and KMS Encryption
Build a secure pipeline to export GuardDuty security findings to an encrypted S3 bucket and automatically ingest them into Splunk for centralized threat monitoring and analysis.
Overview
This project demonstrates how to build a secure, compliance-ready pipeline for exporting AWS GuardDuty security findings to Splunk using S3 bucket storage with KMS encryption. GuardDuty continuously monitors your AWS environment for threats and malicious activity, generating detailed findings that need to be centralized and analyzed.
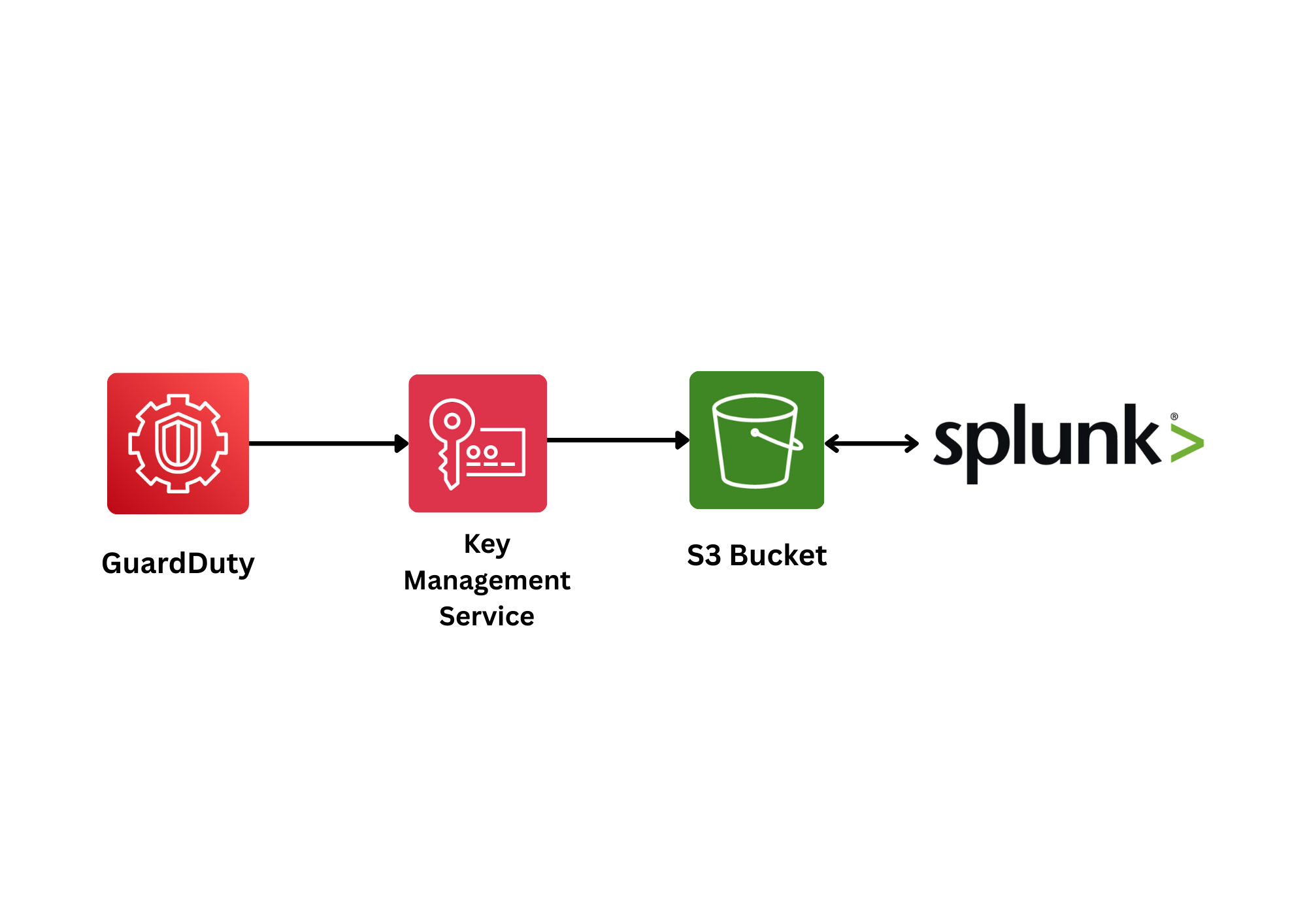
In this implementation, GuardDuty automatically exports findings as JSON files to an encrypted S3 bucket. Splunk's Generic S3 input polls this bucket at regular intervals (typically every 15 minutes) to retrieve and ingest new findings. This batch-processing approach is ideal for organizations that need long-term archival, compliance documentation, and historical analysis of security events.
Key Components
- GuardDuty: Generates security findings from threat detection
- KMS (Key Management Service): Provides encryption keys for securing data at rest
- S3 Bucket: Stores encrypted finding files as durable, long-term archive
- IAM: Manages permissions for GuardDuty to write and Splunk to read
- Splunk Add-on for AWS: Polls S3 and ingests findings into Splunk
When to Use This Pipeline:
- Long-term compliance and audit trail requirements
- Archival storage of all security findings
- Cost-effective solution for moderate alert volumes
- Historical data analysis and reporting
- Acceptable latency of 5-15 minutes for findings
What Makes This Project Valuable?
This pipeline provides a secure, compliant, and cost-effective approach to centralizing GuardDuty findings. By using KMS encryption, you maintain full control over data encryption keys, meeting strict compliance requirements like PCI-DSS, HIPAA, and GDPR. The S3 storage layer ensures findings are never lost and can be reprocessed if needed. This architecture is production-ready and widely adopted in enterprise environments.
What You'll Learn
-
Configure AWS GuardDuty Export Pipeline
Set up GuardDuty publishing destinations to export findings to S3
-
Implement KMS Encryption for S3
Apply key policies to allow GuardDuty and Splunk access
-
Design Secure S3 Bucket Architecture
Configure bucket policies for GuardDuty write and Splunk read access
-
Manage IAM Permissions for Cross-Service Access
Apply least-privilege policies for S3 and KMS operations
Prerequisites
- AWS account with administrative access or permissions to create GuardDuty, KMS keys, S3 buckets, and IAM users
- Splunk Enterprise or Splunk Cloud instance (trial version acceptable)
- Splunk Add-on for Amazon Web Services installed
- Basic understanding of AWS services and security concepts
- Familiarity with JSON policy structure
Lab Environment
Experience hands-on learning with our carefully designed lab environment that mirrors real-world scenarios.
- Real-world tools and interfaces
- Step-by-step guided instructions
- Interactive lab environment
- Hands-on practice with live systems
About Trainer

Aman Gupta
Aman Gupta is an emerging voice in automation-driven cybersecurity, combining strong engineering skills with a passion for knowledge sharing. He has worked on advanced projects spanning security monitoring, intelligent alerting, process automation, and AI-powered decision systems. With experience bridging software engineering and modern DevSecOps practices, Aman focuses on simplifying complex technologies into practical, real-world applications.
Related Projects

Apache Server Log Analysis using Splunk
Detecting Brute Force, SQL Injection, XSS, and Suspicious Web Activity from Apache Access Logs with Splunk SIEM

Practical AWS Cloud Security Posture Assessment Using Scout Suite
Identify real-world AWS attack surfaces through visual security posture analysis.

Wazuh + n8n + Anyrun: Automated Malware Analysis
Automate malware analysis by sending Wazuh-detected suspicious files into ANY.RUN, retrieving detailed reports and IOCs, and integrating results back into your SOC workflow.