Splunk Dashboard for SSH Logs
Building a Real-Time SSH Authentication Monitoring Dashboard
Overview
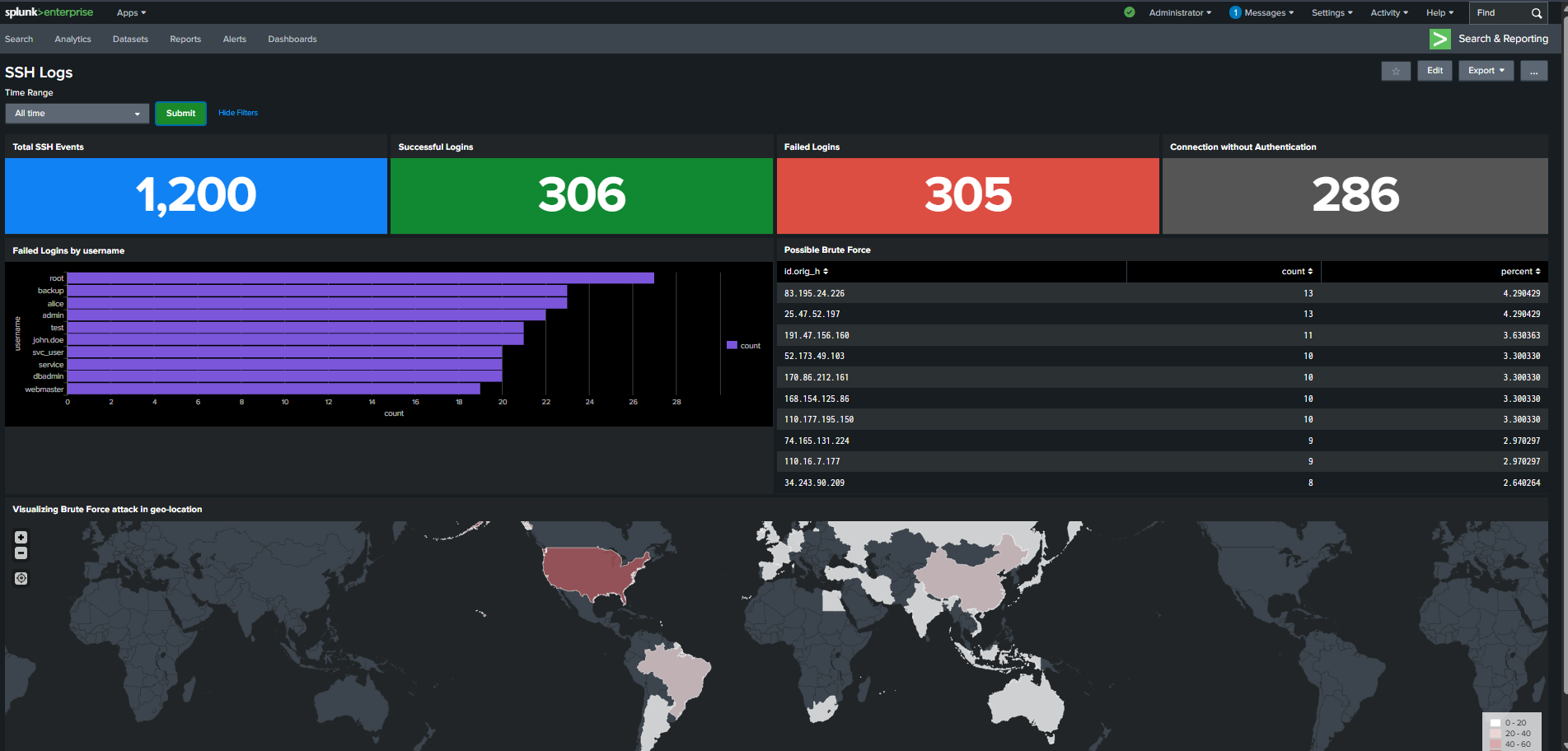
In this project, you'll build a Splunk dashboard for monitoring SSH logs.
The dashboard will visualize login attempts, failed connections, and brute force attacks.
You will create panels for SSH activity summaries and authentication trends.
Geo-location analysis will highlight brute force origins.
A shared time range filter will allow dynamic data exploration.
What You'll Learn
-
Splunk Dashboard Building
Learn how to create interactive dashboards using Splunk's visualization tools.
-
Log Data Analysis
Understand SSH authentication patterns from structured JSON logs.
-
Threat Detection
Identify failed logins and possible brute-force attempts through visual analysis.
-
Geo-Visualization
Map SSH attack origins with Splunk’s choropleth mapping features.
Prerequisites
- Basic knowledge of Splunk Search Processing Language (SPL)
- Access to Splunk Enterprise or Splunk Cloud
- Sample SSH log data in JSON format
Lab Environment
Experience hands-on learning with our carefully designed lab environment that mirrors real-world scenarios.
- Real-world tools and interfaces
- Step-by-step guided instructions
- Interactive lab environment
- Hands-on practice with live systems
About Trainer

Rajneesh Gupta
Rajneesh Gupta is a seasoned cybersecurity professional with over 11 years of industry experience. With a remarkable career focused on incident response, penetration testing, security compliance, and risk management, Rajneesh has established himself as a leading expert in the field. He is also an accomplished author, having penned the book "Hands-on with Blockchain and Cybersecurity". As a dedicated educator, Rajneesh has made a significant impact on the cybersecurity community by training over 60,000 students globally.
Related Projects

Apache Server Log Analysis using Splunk
Detecting Brute Force, SQL Injection, XSS, and Suspicious Web Activity from Apache Access Logs with Splunk SIEM

Practical AWS Cloud Security Posture Assessment Using Scout Suite
Identify real-world AWS attack surfaces through visual security posture analysis.

Wazuh + n8n + Anyrun: Automated Malware Analysis
Automate malware analysis by sending Wazuh-detected suspicious files into ANY.RUN, retrieving detailed reports and IOCs, and integrating results back into your SOC workflow.