DNS Log Analysis using Splunk
Analyse DNS query logs in Splunk to detect anomalies, query patterns, and suspicious activity.
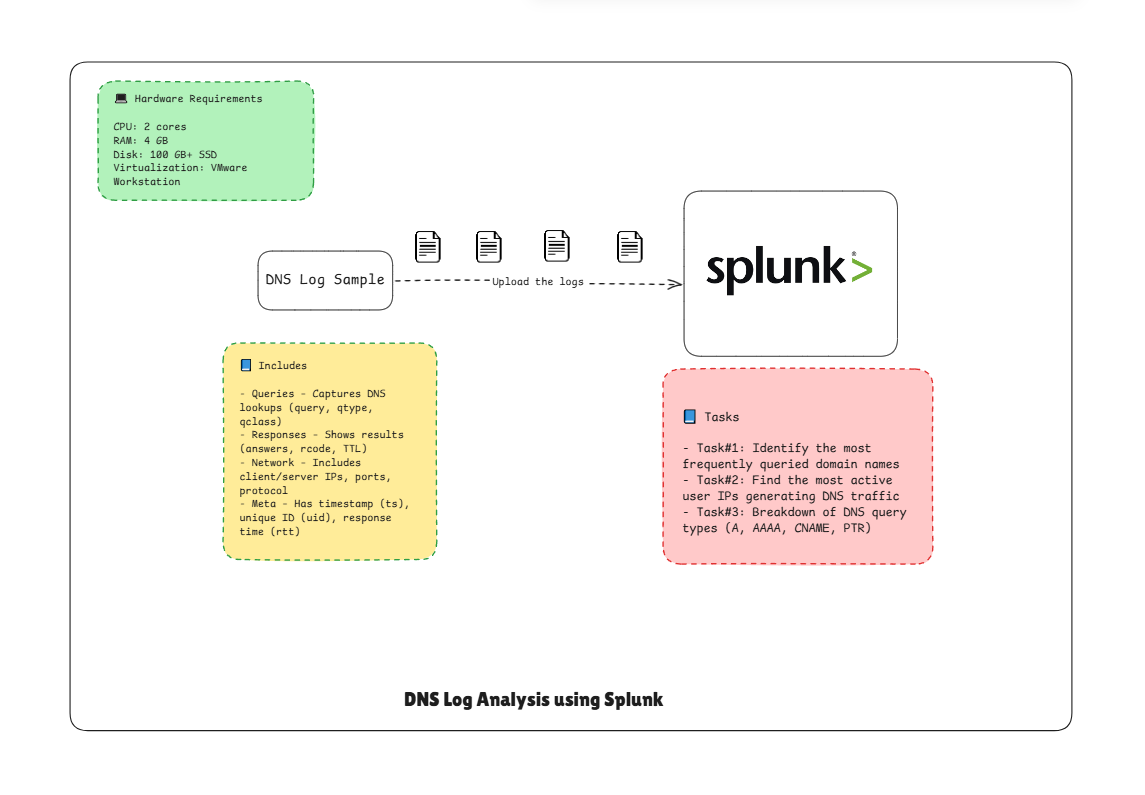
Overview
DNS Log Analysis using Splunk
This project walks you through analyzing DNS query logs in Splunk to detect anomalies, query patterns, and suspicious activity. You’ll ingest sample DNS logs, learn how to detect frequent domains, unusual query types, failed resolutions, and high-latency lookups, and then visualize and alert on them.
- Analyze DNS query types (A, AAAA, CNAME, PTR, MX)
- Identify most frequently queried domains
- Find top clients generating DNS traffic
- Spot failed or suspicious queries (e.g., NXDOMAIN responses)
- Detect high-latency DNS lookups (possible DNS tunneling or misconfigurations)
- Hands-on lab using the provided dns_logs.json dataset
What You'll Learn
-
Log Ingestion & Parsing
How to upload JSON-formatted DNS logs into Splunk and extract relevant fields.
-
Query Analysis
Detect the most queried domains, most active clients, and query distributions.
-
Suspicious Activity Detection
Identify abnormal query types, failed resolutions, and suspicious domains.
-
Performance Monitoring
Spot unusually high response times (rtt) that may indicate DNS tunneling or resolver issues.
Lab Environment
Experience hands-on learning with our carefully designed lab environment that mirrors real-world scenarios.
- Real-world tools and interfaces
- Step-by-step guided instructions
- Interactive lab environment
- Hands-on practice with live systems
About Trainer

Rajneesh Gupta
Rajneesh Gupta is a seasoned cybersecurity professional with over 11 years of industry experience. With a remarkable career focused on incident response, penetration testing, security compliance, and risk management, Rajneesh has established himself as a leading expert in the field. He is also an accomplished author, having penned the book "Hands-on with Blockchain and Cybersecurity". As a dedicated educator, Rajneesh has made a significant impact on the cybersecurity community by training over 60,000 students globally.
Related Projects

Apache Server Log Analysis using Splunk
Detecting Brute Force, SQL Injection, XSS, and Suspicious Web Activity from Apache Access Logs with Splunk SIEM

Wazuh + n8n + Anyrun: Automated Malware Analysis
Automate malware analysis by sending Wazuh-detected suspicious files into ANY.RUN, retrieving detailed reports and IOCs, and integrating results back into your SOC workflow.

Apache Web Server Log Monitoring using Wazuh
Real-time detection of HTTP errors, brute-force and suspicious requests from Apache logs