Detect and Respond SSH Brute-Force attack using Splunk
Building a Real-Time Detection and Automated Response Workflow for SSH Brute-Force Attacks in Splunk SIEM
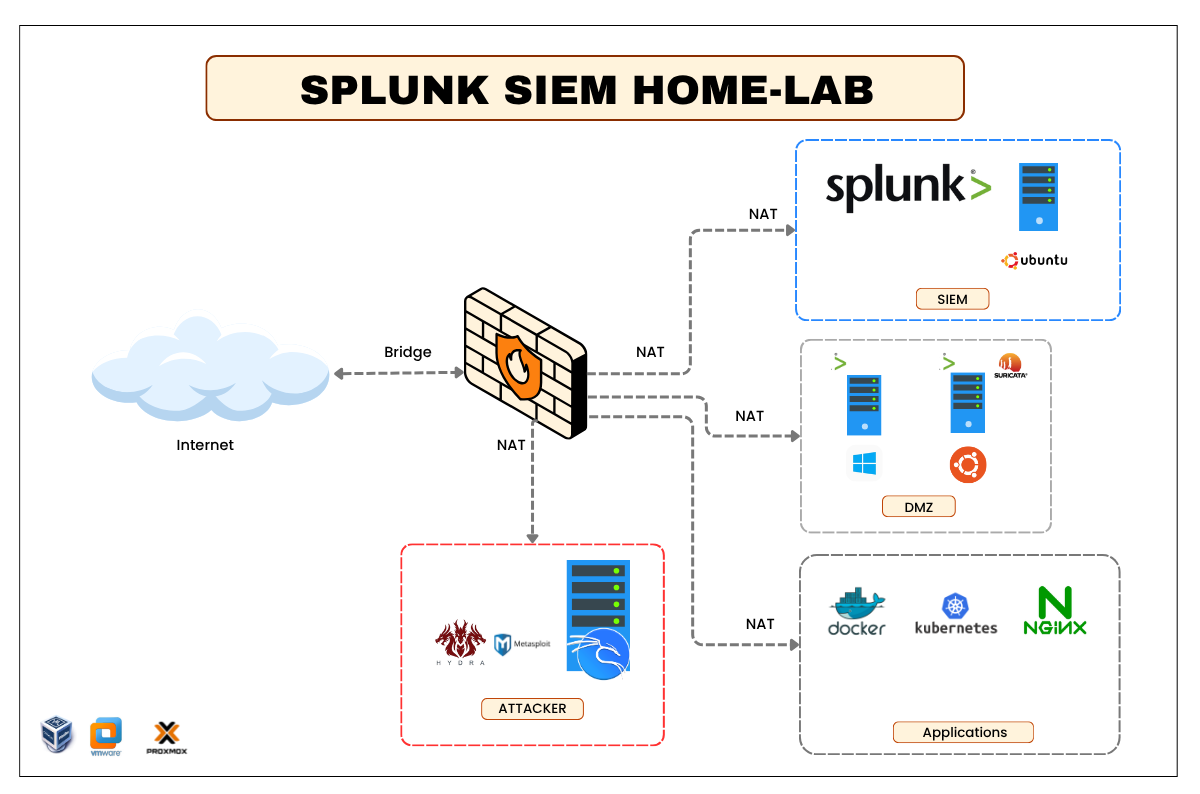
Overview
Simulate credential brute-force attacks against a Linux SSH host and build a complete detection → investigation → response workflow in Splunk.
You will run attacker tooling (Hydra) to generate failed and successful SSH auth events, ingest Suricata network metadata and Linux auth.log into Splunk, author correlation searches and alerts that identify brute-force and password-spray patterns, visualize attacker activity, and implement/verify network/host blocking (ufw/iptables) to prevent further access.
Key outcomes:
- Generate realistic SSH auth event volumes and network IDS metadata.
- Create Splunk searches, saved-search alerts and dashboards to detect attacker IPs and suspicious patterns.
- Investigate attacker sessions and pivot from logs to response.
- Block malicious IP(s) and validate prevention.
What You'll Learn
-
Simulate Attacks
Run Hydra to generate failed/successful SSH auth events for realistic testing.
-
Capture Telemetry
Forward auth.log to index=auth and Suricata eve.json to index=suricata.
-
Detect & Investigate
Create Splunk correlation searches for repeated Failed password and password-spray patterns; pivot on src_ip and user.
-
Respond & Prevent
Block malicious IPs with ufw/iptables and verify prevention.
Prerequisites
- Project: Splunk SIEM Home-Lab
- Ubuntu 22.04 with Splunk Enterprise
- Target: Ubuntu 22.04 running
- Attacker: Kali Linux with `hydra`
Lab Environment
Experience hands-on learning with our carefully designed lab environment that mirrors real-world scenarios.
- Real-world tools and interfaces
- Step-by-step guided instructions
- Interactive lab environment
- Hands-on practice with live systems
About Trainer

Rajneesh Gupta
Rajneesh Gupta is a seasoned cybersecurity professional with over 11 years of industry experience. With a remarkable career focused on incident response, penetration testing, security compliance, and risk management, Rajneesh has established himself as a leading expert in the field. He is also an accomplished author, having penned the book "Hands-on with Blockchain and Cybersecurity". As a dedicated educator, Rajneesh has made a significant impact on the cybersecurity community by training over 60,000 students globally.
Related Projects

Apache Server Log Analysis using Splunk
Detecting Brute Force, SQL Injection, XSS, and Suspicious Web Activity from Apache Access Logs with Splunk SIEM

Wazuh + n8n + Anyrun: Automated Malware Analysis
Automate malware analysis by sending Wazuh-detected suspicious files into ANY.RUN, retrieving detailed reports and IOCs, and integrating results back into your SOC workflow.

Apache Web Server Log Monitoring using Wazuh
Real-time detection of HTTP errors, brute-force and suspicious requests from Apache logs