AWS GuardDuty logs Ingestion in Splunk
Build a near real-time event-driven pipeline to stream GuardDuty security findings through EventBridge, SNS, and SQS into Splunk for immediate threat detection and incident response.
Overview
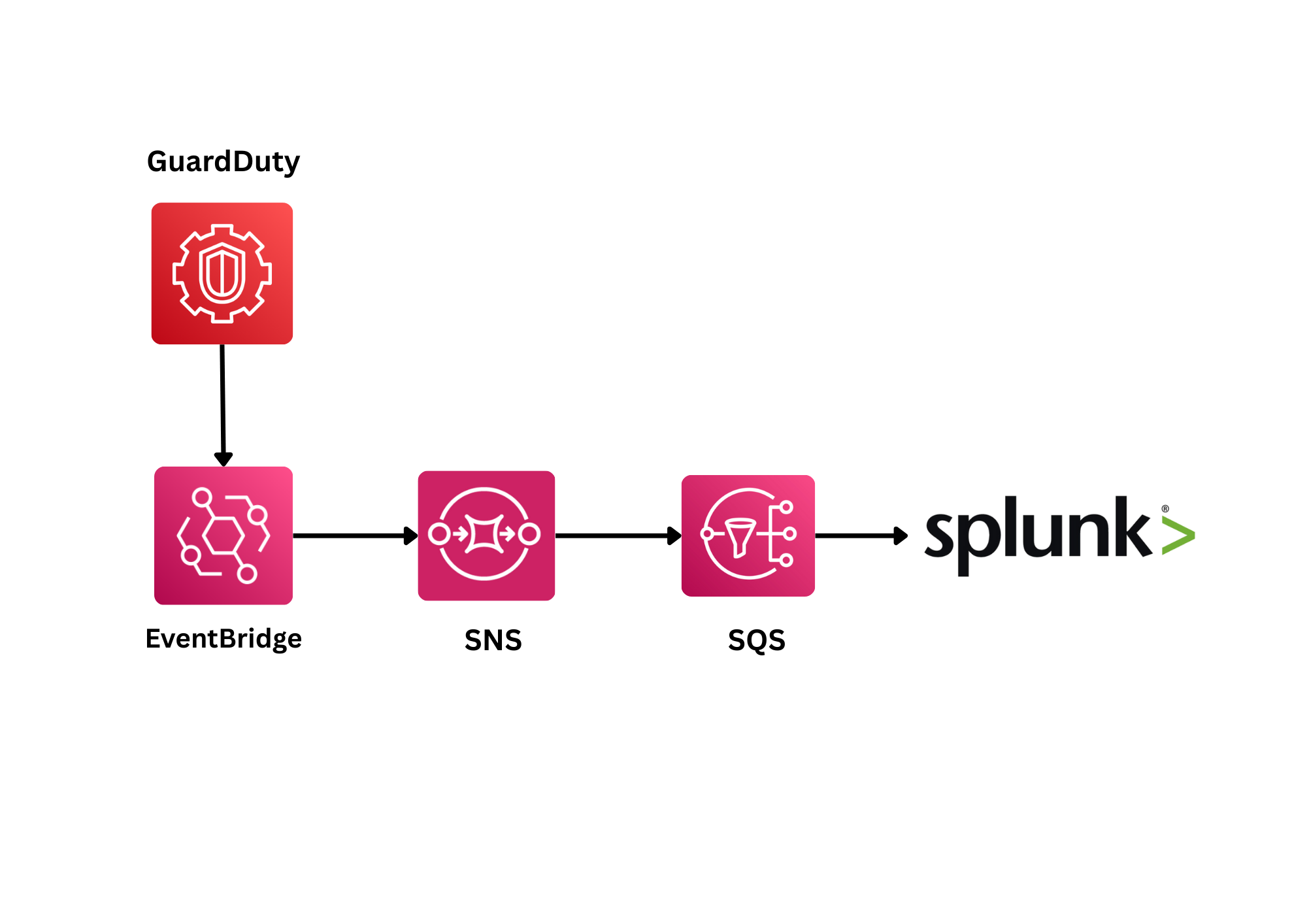
This project showcases an event-driven, real-time architecture for streaming AWS GuardDuty findings into Splunk with sub-minute latency. Modern security operations require immediate visibility into threats, and this pipeline delivers findings to your SIEM within seconds of detection.
The architecture leverages Amazon EventBridge to capture GuardDuty findings as they occur, routes them through SNS for flexible message distribution, buffers them in SQS for reliable delivery, and finally streams them into Splunk. This approach is essential for Security Operations Centers (SOCs) that need to detect and respond to threats immediately, trigger automated remediation workflows, or meet strict security SLAs.
Key Components:
- GuardDuty: Generates security findings in real-time
- EventBridge: Captures events using pattern matching and routes to targets
- SNS (Simple Notification Service): Distributes notifications to multiple subscribers
- SQS (Simple Queue Service): Buffers messages for reliable, decoupled delivery
- IAM: Manages permissions across all services
- Splunk Add-on for AWS: Continuously polls SQS and ingests messages
When to Use This Pipeline:
- Real-time security alerting (seconds, not minutes)
- Immediate incident response and SOAR integration
- Multiple consumers processing the same findings (via SNS fanout)
- Event-driven automation and workflows
- Strict security SLAs requiring fast detection
What Makes This Project Valuable?
This pipeline represents modern, cloud-native security architecture patterns. By decoupling event producers (GuardDuty) from consumers (Splunk) using EventBridge, SNS, and SQS, you build a resilient system that can scale to handle thousands of findings per hour. The message buffering in SQS ensures no findings are lost even if Splunk is temporarily unavailable. This architecture is commonly used by enterprises running 24/7 SOCs and enables advanced use cases like multi-region threat correlation and automated incident response.
What You'll Learn
-
Design Event-Driven Security Architectures
Configure EventBridge rules to capture GuardDuty findings using event patterns
-
Implement SNS and SQS Message Queuing
Set up SQS queues with proper subscriptions for reliable message buffering
-
Build EventBridge Rules with Pattern Matching
Use the EventBridge visual pattern builder to filter AWS service events
-
Configure Cross-Service IAM Permissions
Understand automatic policy updates during SNS-SQS subscriptions
-
Set Up Real-Time SIEM Integration
Verify end-to-end message flow and troubleshoot pipeline issues
Prerequisites
- AWS account with permissions to create EventBridge rules, SNS topics, SQS queues, and IAM users
- Splunk Enterprise or Splunk Cloud instance (trial version acceptable)
- Splunk Add-on for Amazon Web Services installed
- Basic understanding of event-driven architectures and message queuing
- Familiarity with AWS security services
Lab Environment
Experience hands-on learning with our carefully designed lab environment that mirrors real-world scenarios.
- Real-world tools and interfaces
- Step-by-step guided instructions
- Interactive lab environment
- Hands-on practice with live systems
About Trainer

Aman Gupta
Aman Gupta is an emerging voice in automation-driven cybersecurity, combining strong engineering skills with a passion for knowledge sharing. He has worked on advanced projects spanning security monitoring, intelligent alerting, process automation, and AI-powered decision systems. With experience bridging software engineering and modern DevSecOps practices, Aman focuses on simplifying complex technologies into practical, real-world applications.
Related Projects

Apache Server Log Analysis using Splunk
Detecting Brute Force, SQL Injection, XSS, and Suspicious Web Activity from Apache Access Logs with Splunk SIEM

Practical AWS Cloud Security Posture Assessment Using Scout Suite
Identify real-world AWS attack surfaces through visual security posture analysis.

Wazuh + n8n + Anyrun: Automated Malware Analysis
Automate malware analysis by sending Wazuh-detected suspicious files into ANY.RUN, retrieving detailed reports and IOCs, and integrating results back into your SOC workflow.