Splunk SIEM Home-Lab
Build and Configure a Complete Threat-Detection Environment using Splunk, Suricata IDS, and Attacker Simulations
Overview
Project Overview: Splunk SIEM Home-Lab
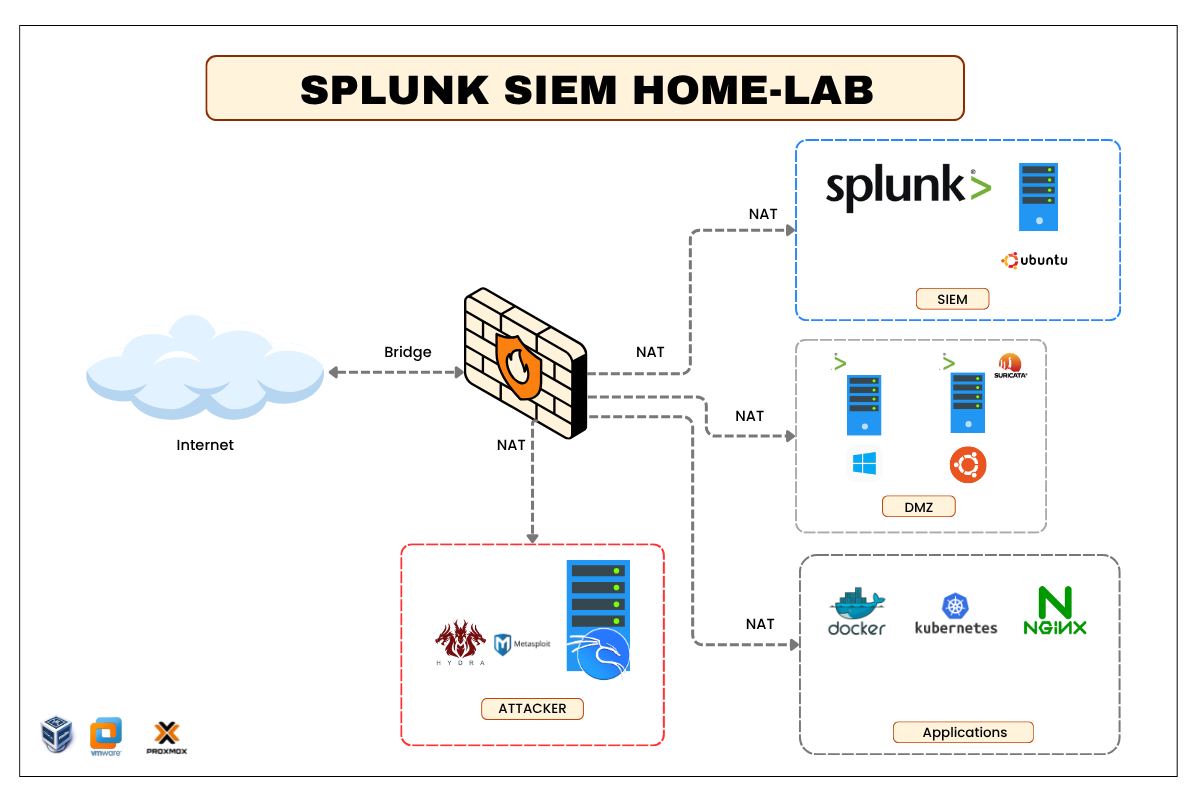
This project guides you through building your own Splunk SIEM environment for real-time log collection, correlation, and visualization. You’ll set up Splunk Enterprise on Ubuntu, integrate Suricata IDS for network intrusion detection, onboard Windows and Linux endpoints as log sources, and simulate attacks using Kali Linux tools such as Hydra and Metasploit.
- Enterprise-grade SIEM platform for security analytics
- Real-time event ingestion and search-driven correlation
- Integration with Suricata for IDS alert visualization
- Centralized monitoring for Windows, Linux, and Docker environments
- Attack simulation with Kali Linux for detection validation
- Deployable on VMware, VirtualBox, or Proxmox
What You'll Learn
-
Splunk Installation & Setup
Install and configure Splunk Enterprise on Ubuntu for log collection and analytics.
-
Universal Forwarder Deployment
Deploy Splunk Universal Forwarders on Windows and Linux hosts to forward logs securely.
-
Suricata IDS Integration
Connect Suricata IDS alerts and logs into Splunk for network-based intrusion visibility.
-
Threat Simulation & Detection
Use Kali Linux with Hydra and Metasploit to simulate brute-force and exploitation attacks.
Prerequisites
- Basic understanding of Linux and networking
- Virtualization platform: VMware, VirtualBox, or Proxmox
- Minimum 8 GB RAM and 4 vCPUs recommended for full lab
Lab Environment
Experience hands-on learning with our carefully designed lab environment that mirrors real-world scenarios.
- Real-world tools and interfaces
- Step-by-step guided instructions
- Interactive lab environment
- Hands-on practice with live systems
About Trainer

Rajneesh Gupta
Rajneesh Gupta is a seasoned cybersecurity professional with over 11 years of industry experience. With a remarkable career focused on incident response, penetration testing, security compliance, and risk management, Rajneesh has established himself as a leading expert in the field. He is also an accomplished author, having penned the book "Hands-on with Blockchain and Cybersecurity". As a dedicated educator, Rajneesh has made a significant impact on the cybersecurity community by training over 60,000 students globally.
Related Projects

Wazuh + n8n + Anyrun: Automated Malware Analysis
Automate malware analysis by sending Wazuh-detected suspicious files into ANY.RUN, retrieving detailed reports and IOCs, and integrating results back into your SOC workflow.

Threat Hunting Home-Lab(using Velociraptor)
Deploy, Configure, and Hunt Threats with Velociraptor Forensics Platform

AWS GuardDuty Findings Ingestion in Splunk using S3 and KMS Encryption
Build a secure pipeline to export GuardDuty security findings to an encrypted S3 bucket and automatically ingest them into Splunk for centralized threat monitoring and analysis.